Cryptographic Agility: Why is it important?
Most businesses look at the dire warnings that internet security will soon be broken due to quantum computing with a healthy bit of skepticism. To most businesses the threat appears to be years away and will likely be solved during the normal course of system update cycles. Is this view justified?
Adding to the noise around quantum cryptography is the May 4th 2022 US Executive Order focused on quantum computing and mitigating risks related vulnerable cryptographic systems. The executive order required a working group with industry inclusive of critical infrastructure and within NIST a post quantum project within 90 days of the order which added an urgency not usually seen.
National Security Memorandum on Promoting United States Leadership in Quantum Computing While…
NATIONAL SECURITY MEMORANDUM/NSM-10 MEMORANDUM FOR THE VICE PRESIDENT THE SECRETARY OF STATE THE SECRETARY OF THE…
The problem posed by quantum computers and internet security is that that using the Shor’s algorithm on a sufficiently powerful quantum computer vastly decreases the time needed to perform prime integer factorization, breaking the mathematical basis for public-key cryptography such as RSA, Diffie-Hellman and Elliptic Curve Diffie-Helman.
Shor’s algorithm – Wikipedia
Shor’s algorithm is a quantum computer algorithm for finding the prime factors of an integer. It was developed in 1994…
Current predictions show it will be more than 10 years before the threat is significant. Currently the number of qubits quantum computers have are insufficient to cause a problem, but rapid progress is being made. Currently IBM has the largest known quantum computer at 127 qubits and is expected to reach 1121 qubits in 2023. Thankfully this is still well below the near 5,000 qubits needed to crack RSA at 2048 bits.
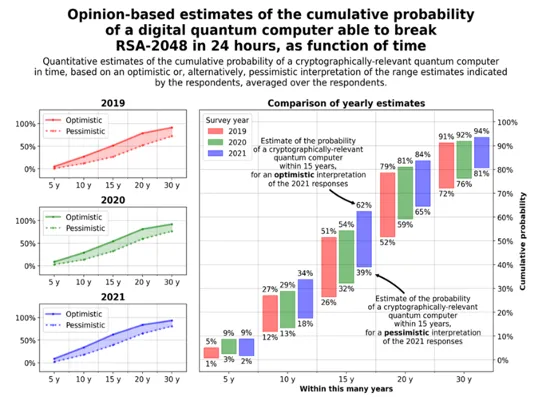
2021 Quantum Threat Timeline Report – Global Risk Institute
Computational problems, previously thought to be intractable by any reasonable means with potentially catastrophic…
Given the timeline, why should anybody bother to address the problem now? Simple, based directly on the last time cryptographic protocols were updated, it’s expected to take 10 years to complete the transition. This timeline plays directly against the data shelf life and system lifetime associated with the information the business is protecting. Short shelf-life data with short system lifetimes are of lower risk as opposed to long shelf-life data with long system lifetimes have significantly greater risk.
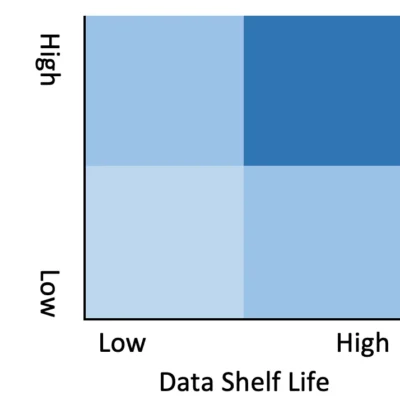
What should companies do? First inventory how and where systems use cryptography with risk prioritization based on the lifetime of the data and systems. Secondly start working on putting cryptographic agility into your applications now. Cryptographic agility solves real world issues companies have now such as providing centralized ability to modify key lengths, algorithms, reporting, and depending on the implementation can provide mutual, segmentation, and authentication without application changes to support cloud migration and systems transformation. By fixing current real-world problems you also are set to rapidly adopt quantum safe algorithms when they are ready for primetime.




