Workload Security Capabilities
Shift Up and Shift Left
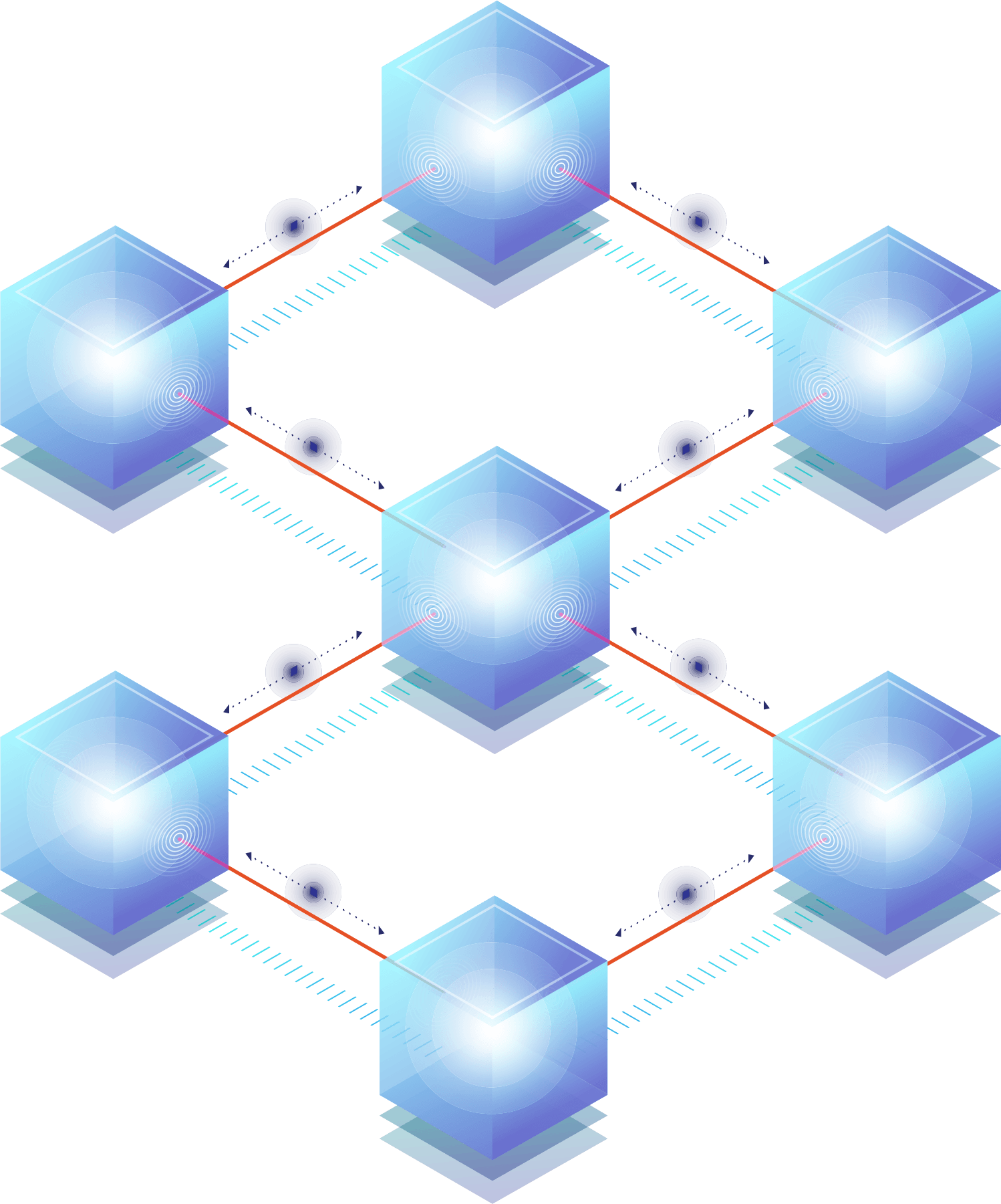
Workload attack surface protection requires authentication, authorization, auditing, and isolation while ensuring compliance but existing solutions are too complex, incomplete, and expensive.
TrustFour infuses controls to protect Workloads without requiring code changes to dramatically reduce the attack surface while lowering cost and complexity.
TrustFour shifts ownership up and left from the Network and NetOps to the Applications and DevOps aligning responsibility and ensuring scale.
0
k
Subdomains
0
%
bad ciphers
0
%
Quantum Support
Fortune 500 TLS Compliance
TrustFour Scanned the Internet